During the continuing Coronavirus pandemic and the resulting uncertainty, stress and unemployment, scammers are seeing an opportunity to scam unsuspecting victims and take financial advantage of their plight. From “free government grants” to “the cure for coronavirus”, the next email you open could well be an attempt to extort you of thousands of pounds.
Phishing is still the biggest cyber threat to organisations. It’s popular with everyone from financially motivated criminal gangs to state-sponsored espionage groups. And all for one simple reason: it works. According to the annual Data Breach Investigations Report, phishing had by far the highest success rate of any threat vector. During the past year, despite being the primary threat action in less than 10% of security incidents, phishing was the primary weapon in almost a third (32%) of all data breaches.
Top COVID-19 email scams to look out for
- Fake government emails offering grants of up to £7,500. Clicking on the links allows scammers to steal personal and financial information.
- Scam emails offering access to “COVID-19 relief funds”
- Official-looking emails offering a “council tax reduction”
- Benefit recipients are offered help in applying for universal credit, but fraudsters grab some of the payment as an advance for their “services”
- Phishing emails claiming that the recipient has been in contact with someone diagnosed with COVID-19
- Fake adverts for non-existent coronavirus-related products
- Fake emails and texts claiming to be from TV Licensing, offering six months free but asking people to update their payment information
- Emails asking people to update their TV subscription services payment details by clicking on a link
- Fake profiles on social media sites are used to manipulate victims into handing over their money
- Fake investment opportunities are advertised on social media sites, encouraging victims to “take advantage of the financial downturn”
How to avoid email bait
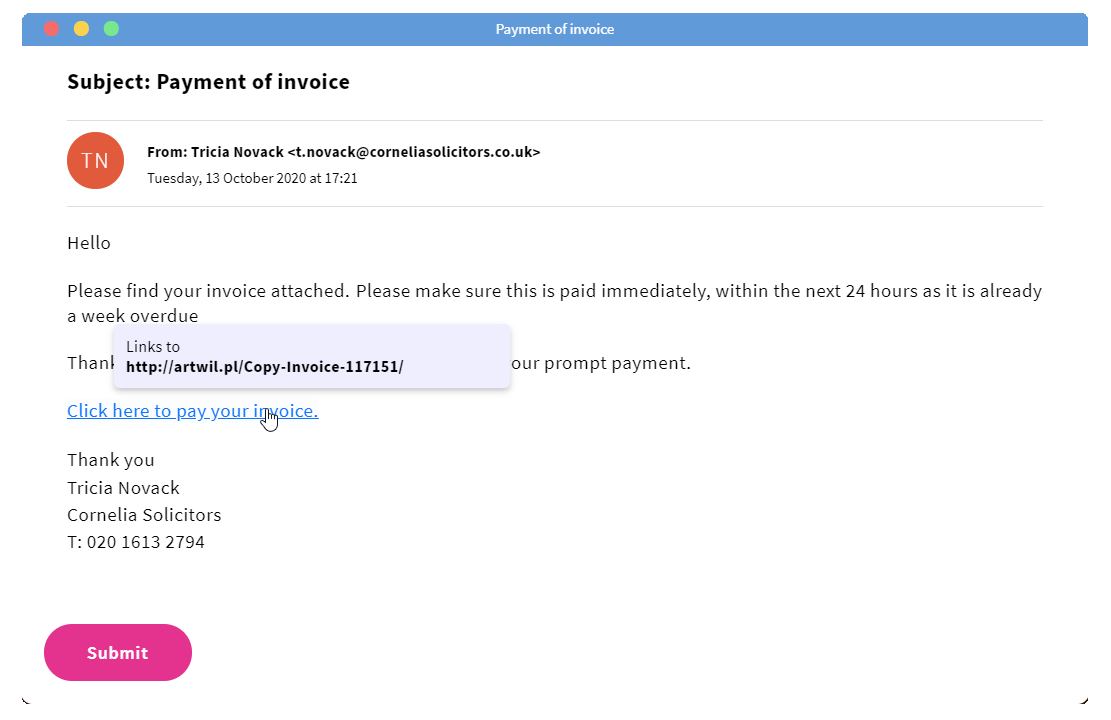
Do the hyperlinks make sense?
Clicking on the wrong link can lead to malware being installed on your computer, malicious emails sent to your contacts, or attackers gaining sensitive personal information. Make sure you don’t click on any links in a suspicious email. You should also avoid clicking on a link that looks strange to you. Simply hover over the hyperlink, check it begins with “https” and if anything doesn’t make sense, don’t click on the link.
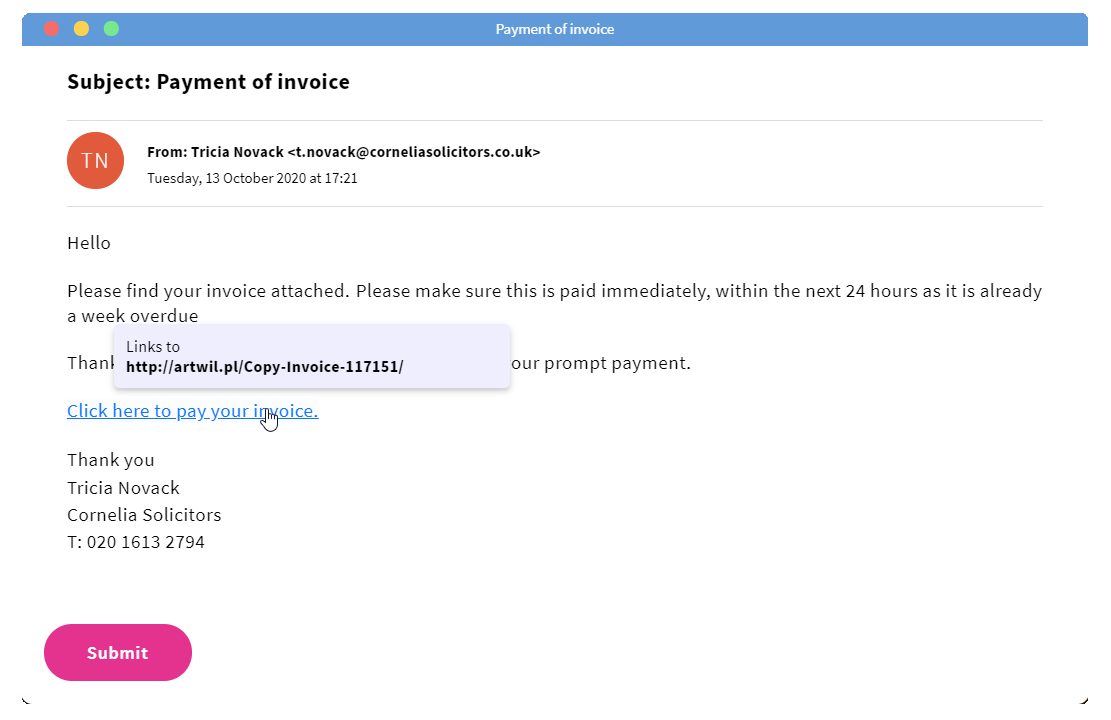
How is the email written?
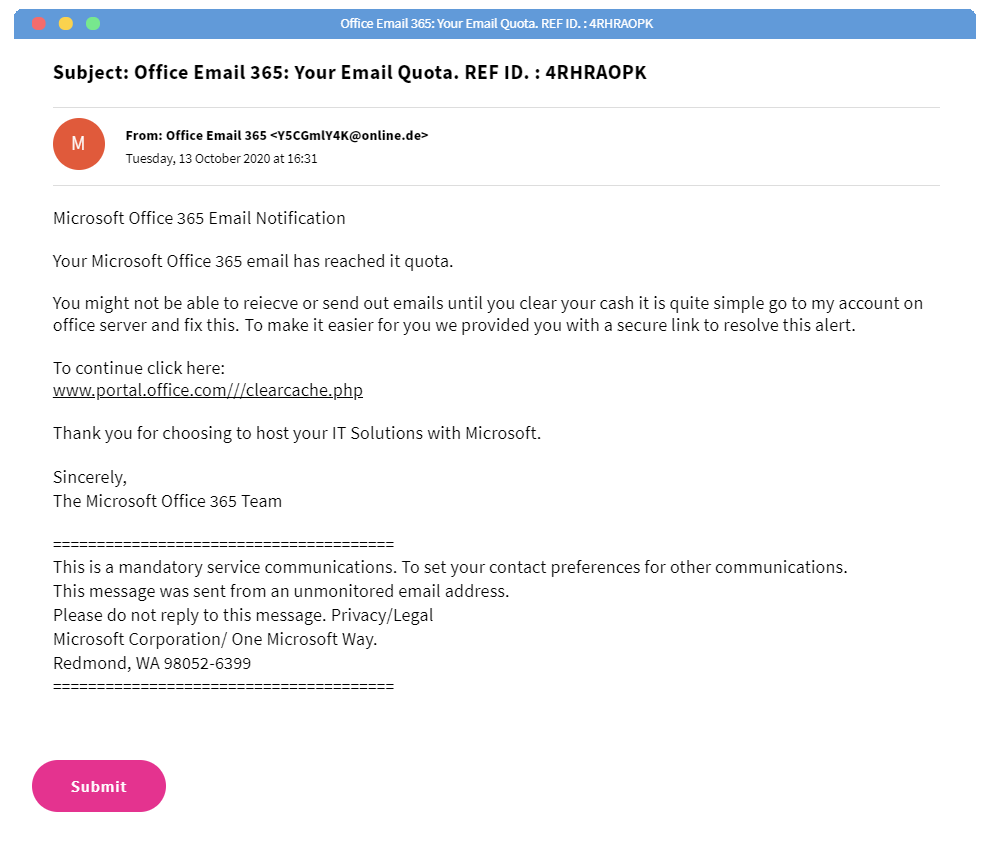
The way an email is written can be very helpful in trying to tell a phishing email apart from an innocent email. Ask yourself:
- Does the email carry an urgent tone (e.g. “I need you to send me this information in the next 24 hours”)?
- Does the sender use poor grammar or language that is inconsistent with who they are claiming to be?
- Are they offering something that seems too good to be true?
- Is there any threatening language?
If any of the above red flags exist, the email should go straight into your spam file.
What’s in the “to” and “from” fields?
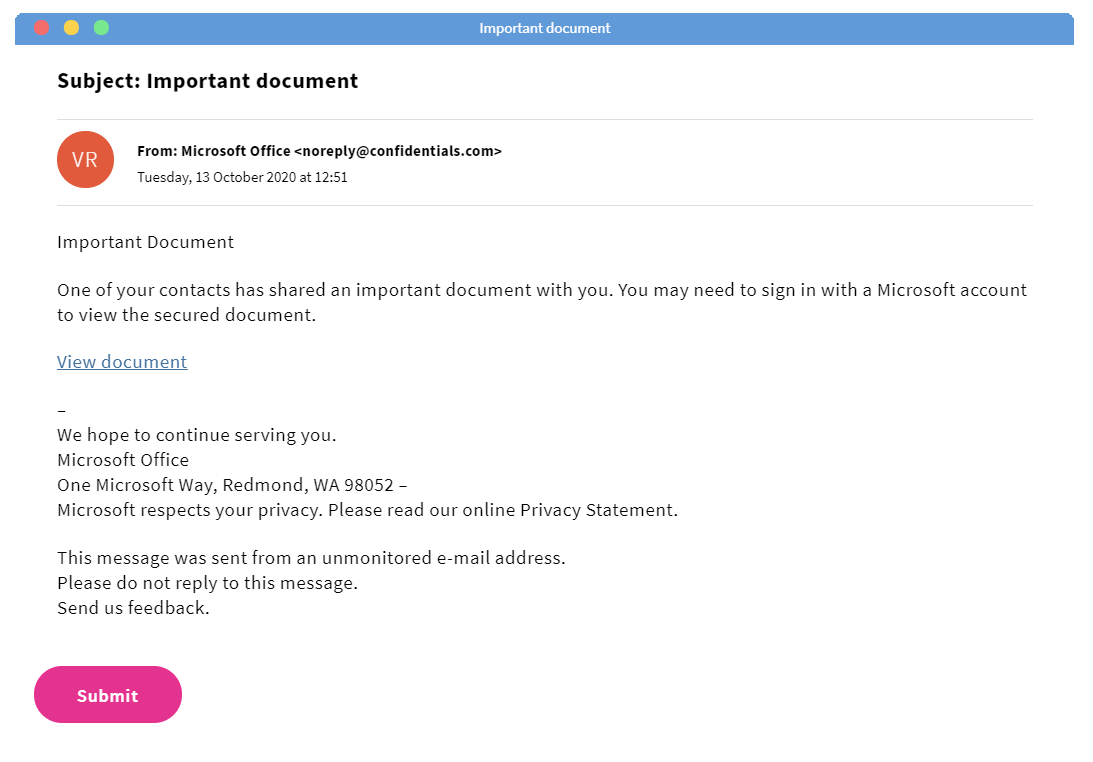
Examine the “to” and “from” fields. If they are both the same, this means the email wasn’t designed for you and you should ignore it. You should also ensure the “from” email address is accurate according to the “from” name. Further, if there are a lot of random recipients whose names and email addresses seem unfamiliar, this could be a sign that a hacker is trying to send a mass phishing email.
Does the email contain suspicious attachments?
Downloading an unsolicited attachment can infect your system with malware. If you are asked to download an attachment such as a Zip file from an email address you don’t recognise, or the email itself looks suspicious (for example if it contains any of the red flags listed above), be sure not to download the attachment.
Are you being asked for personal information?
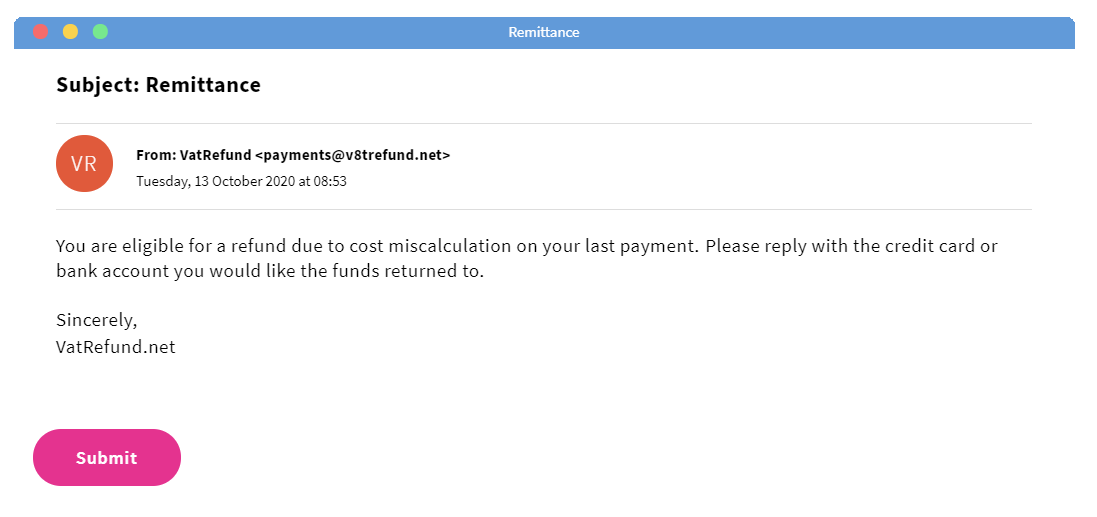
An innocent email would never ask for personal information, such as a date of birth, password or credit card information. An example of this could be an urgent email claiming your bank account has been hacked and asking you to provide your bank details to confirm your identity.
Is someone asking you for money?
If you receive an email from a relative or friend saying they desperately need £5,000 to get them out of a sticky situation, pick up the phone and call them directly – the email is most likely a scam.
Remember, it is always better to be safe than sorry. If something doesn’t seem right, it probably isn’t, and if an offer seems too good to be true, it probably is.
VinciWorks’ email awareness training
VinciWorks’ cyber security training suite includes several units and individual courses covering how to protect yourself when using email. The training can be taken both as one-off training units or as part of a multi-year cyber awareness training plan.
Cyber Security: Journey to Safety
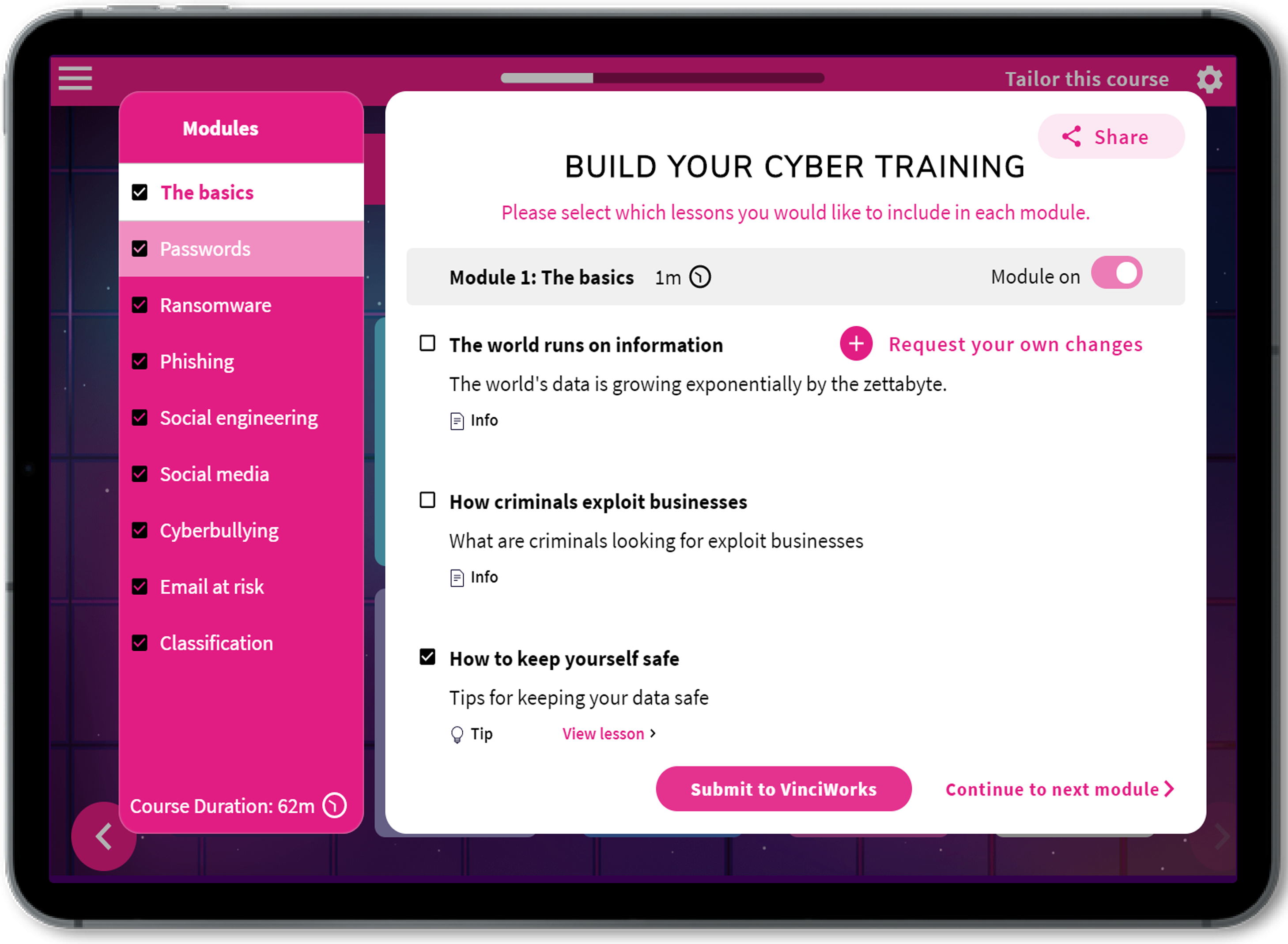
This course takes personalisation to the next level. Using our builder, you can dynamically configure the training to cover topics relevant to your organisation. If you wish to roll out email-related units to your staff, for example, we recommend customising the course to include our phishing, social engineering and Email@Risk modules.
Email@Risk
This 10 minute course is designed to help users understand the risks presented by email and how to take action to mitigate them.
Phishing Challenges
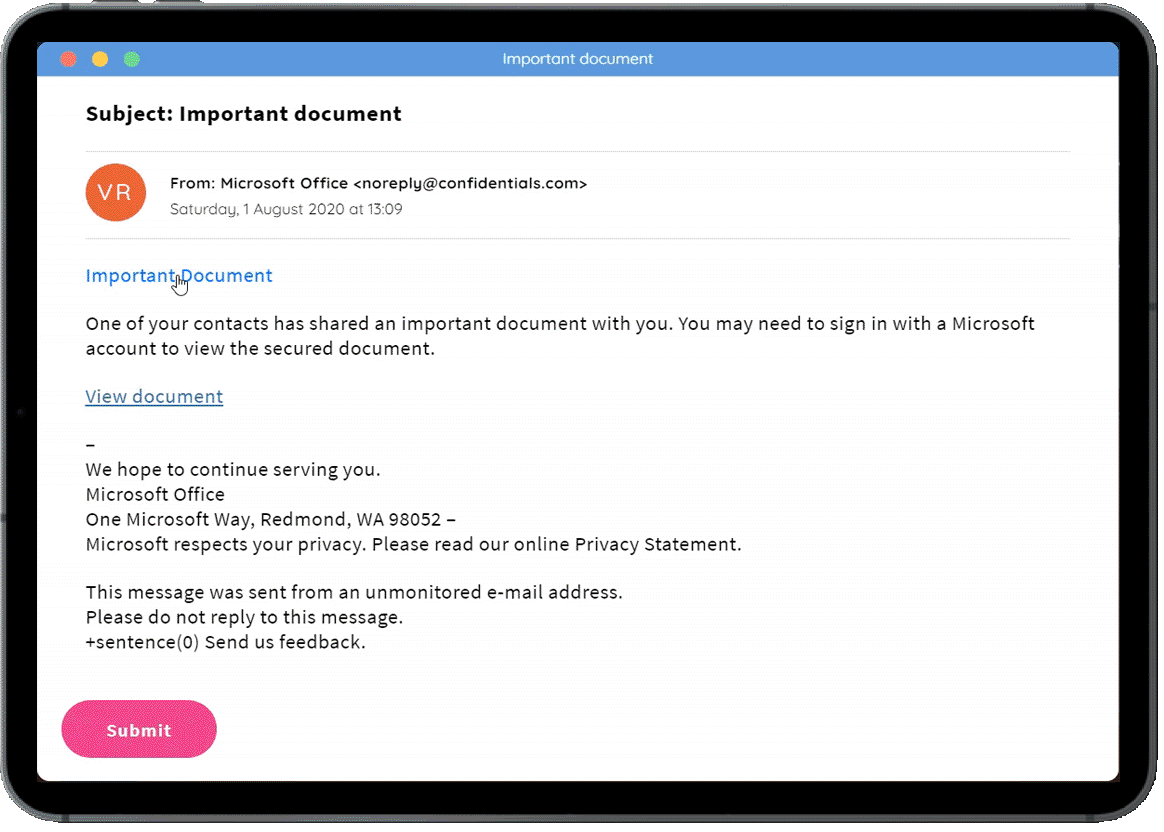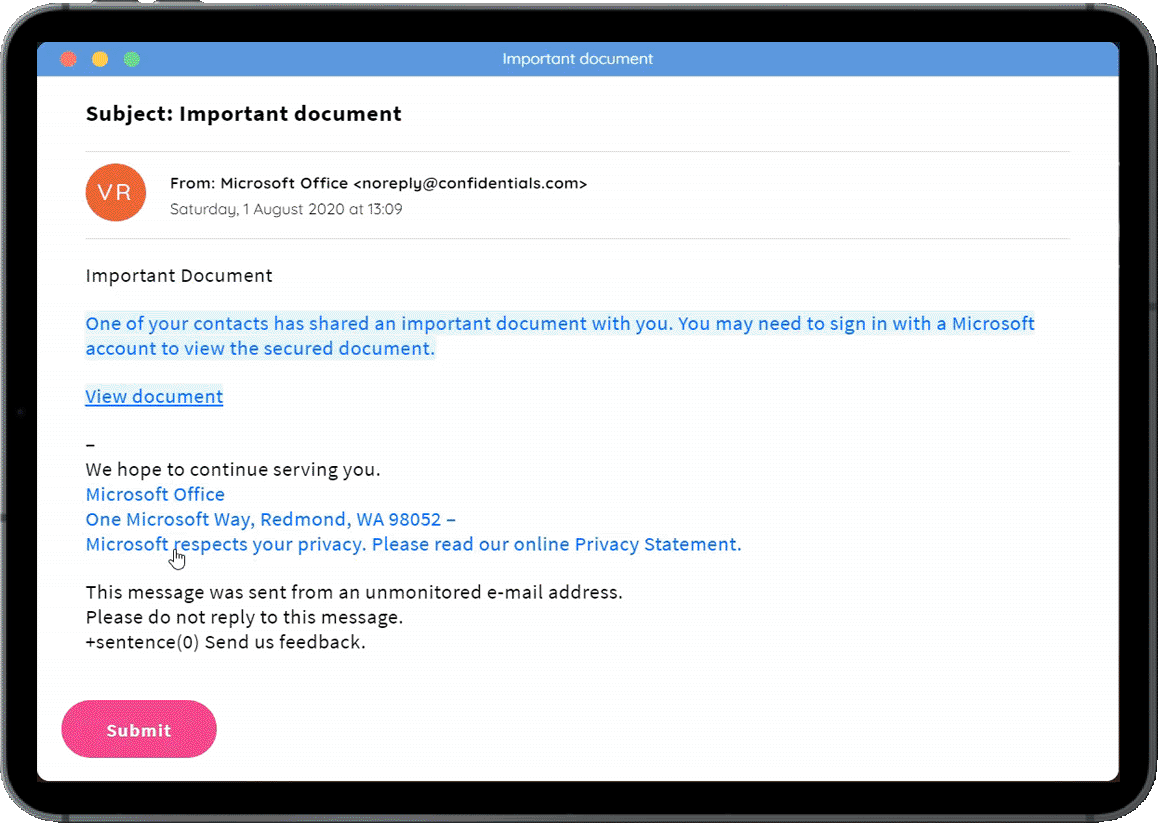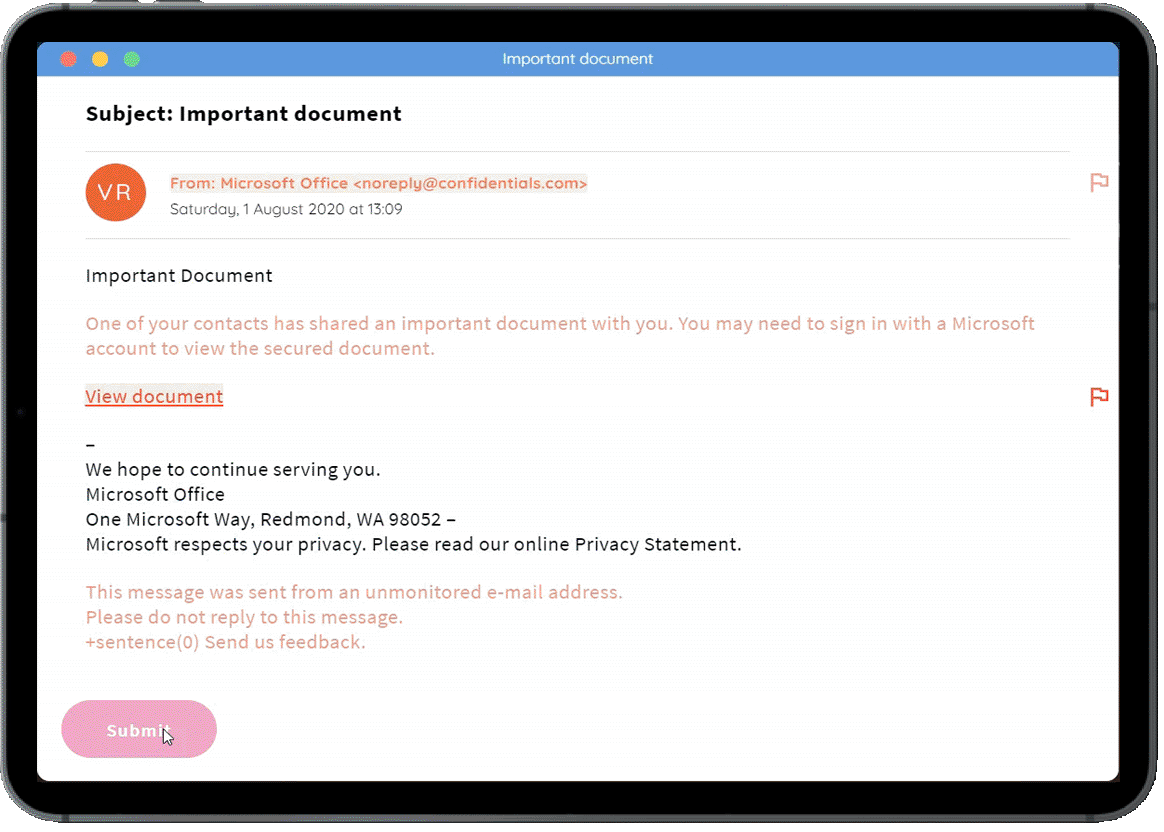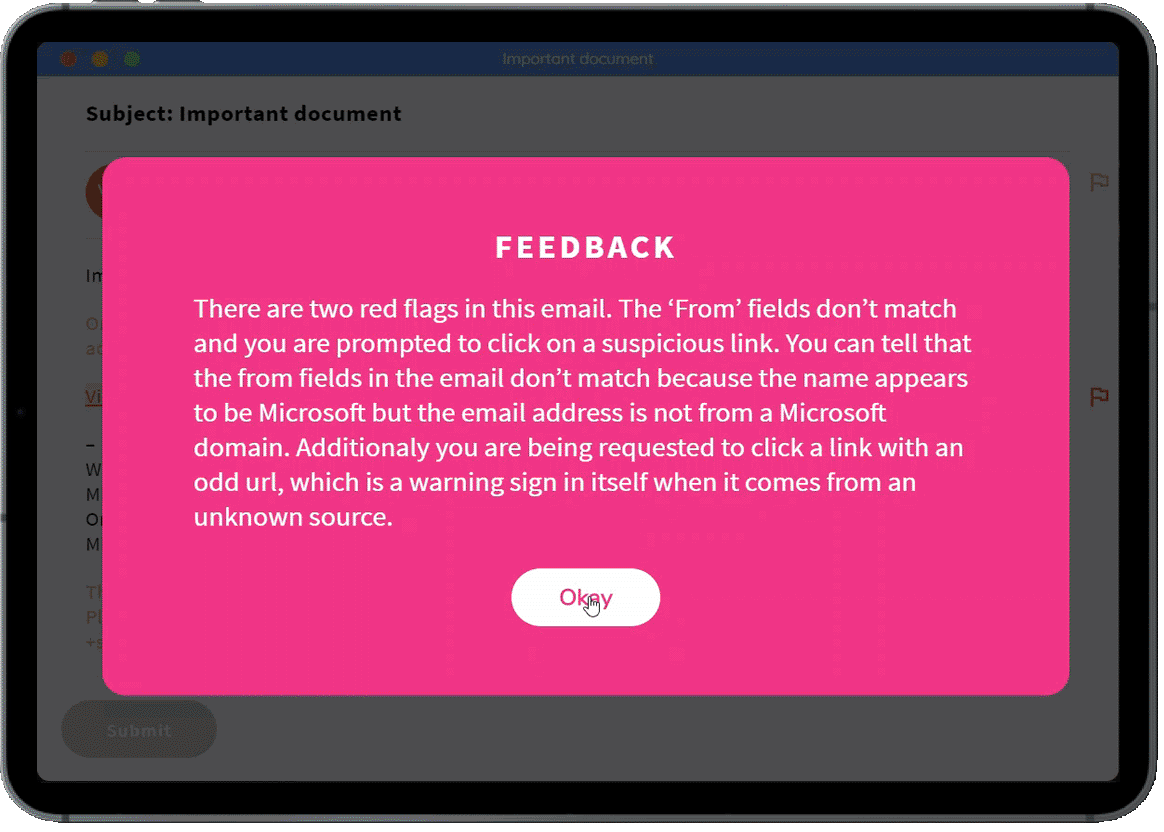
Our phishing challenges present a series of emails, with users having to identify the red flags in each one. We regularly add new phishing challenges covering the latest threats.
Phishing Knowledge Check
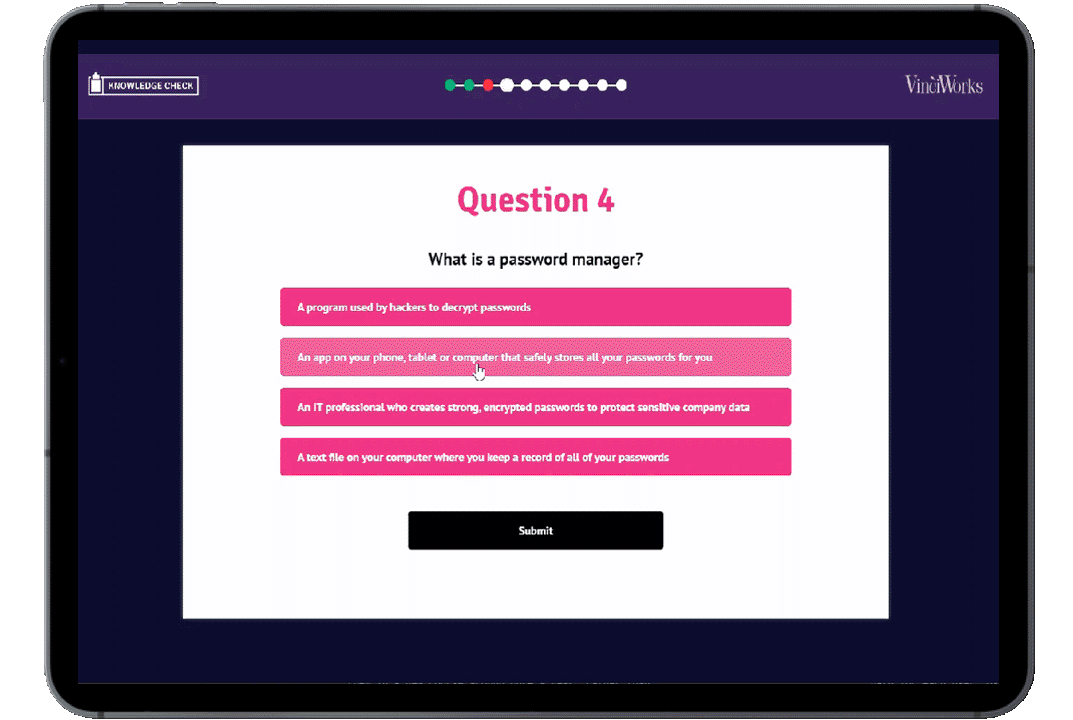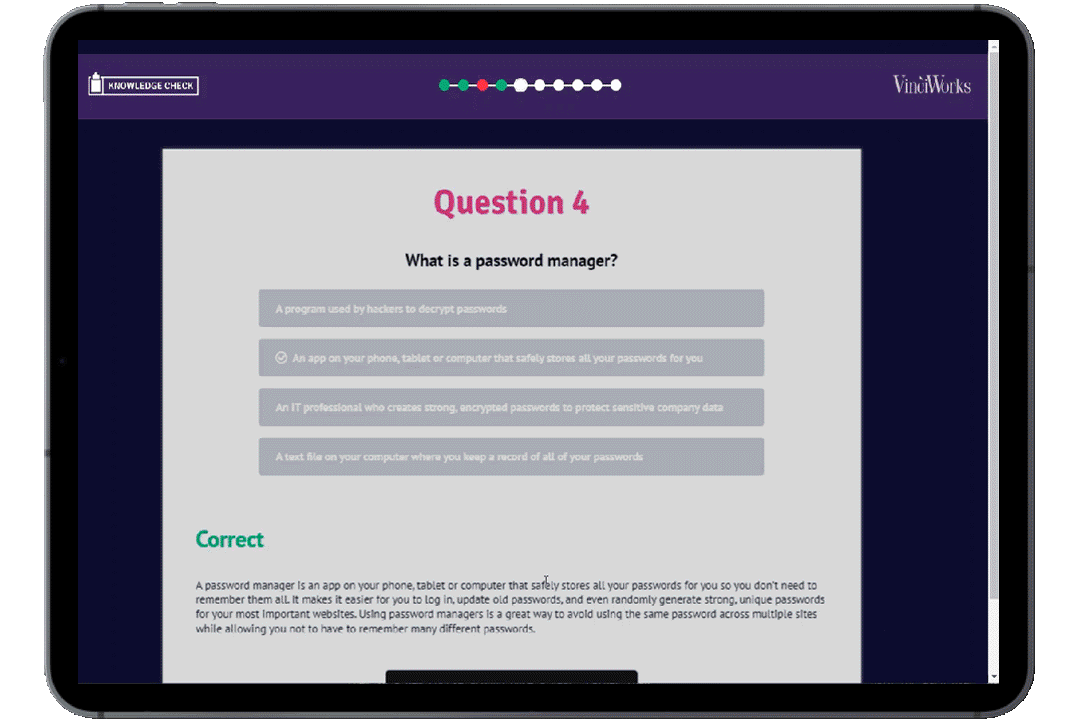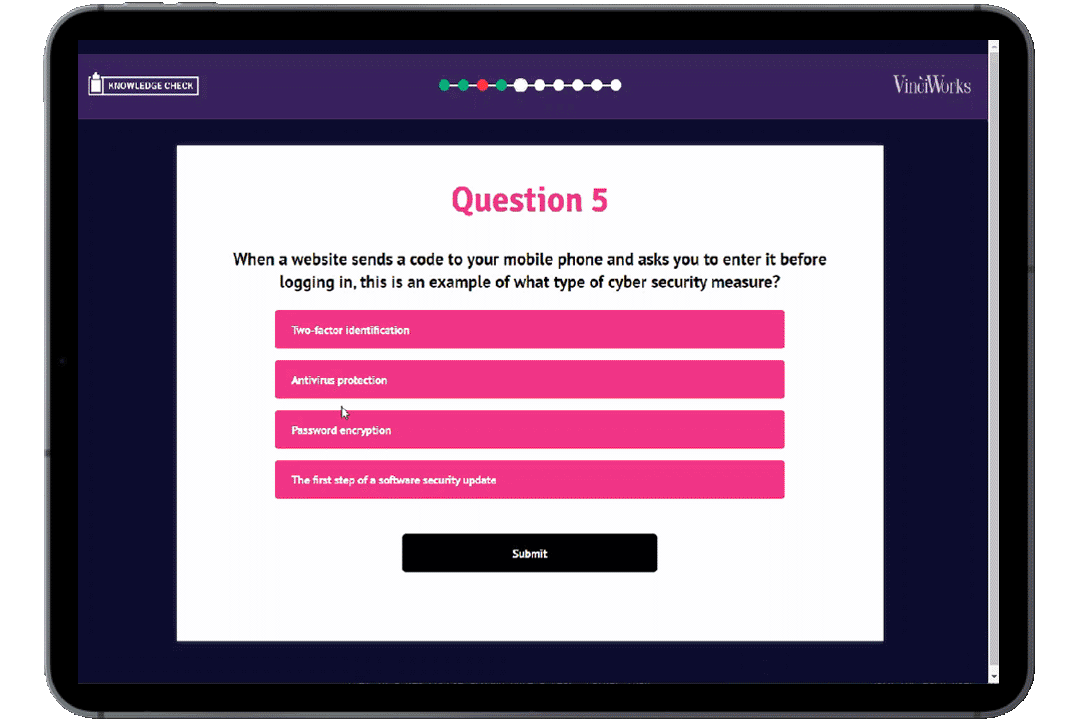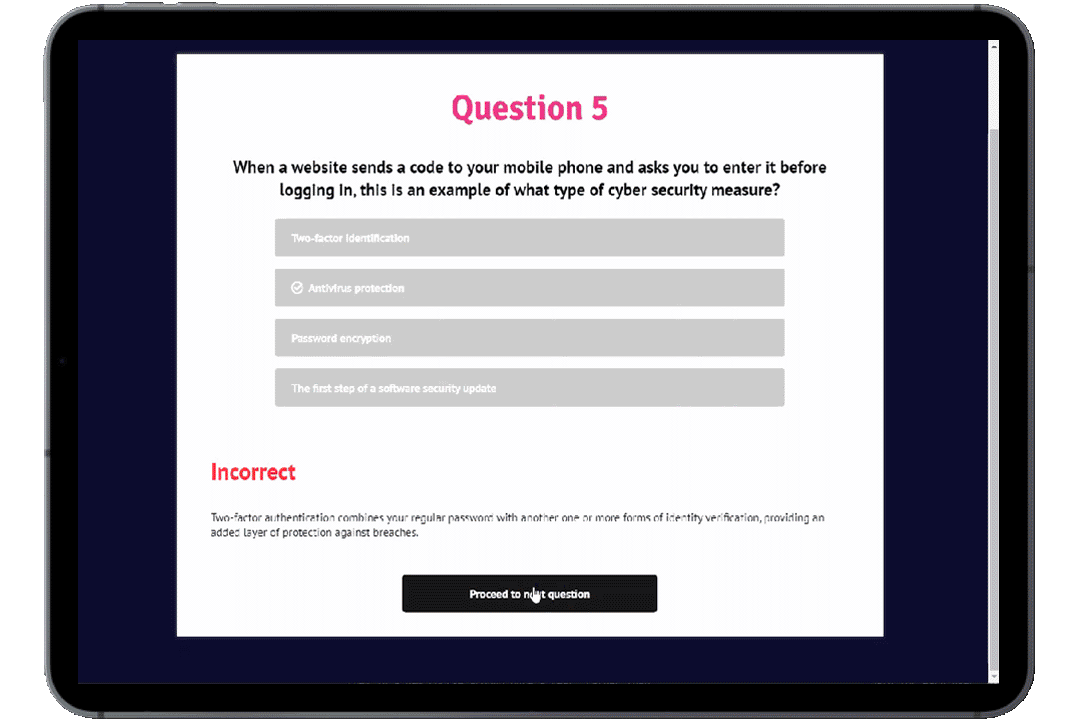
Our phishing knowledge checks assess users’ understanding of the core risks presented by potential phishing attacks. Each knowledge check contains ten questions, with the user receiving instant feedback on each answer. They can be used by admins and managers to better understand their staff’s understanding of the topic and whether more in-depth training is required.