Since the EU’s General Data Protection Regulation (GDPR) came into force three years ago, there have been fines reaching a total of over €280 million, the UK left the EU and the ICO has announced that there will be a new Commissioner from October.
The ICO (Information Commissioner’s Office) is the UK’s independent authority set up to uphold information rights. The organisation aims to promote openness by public bodies and data privacy for individuals. Part of their role is to help ensure organisations meet their information rights obligations and take action when they don’t.
What can we learn from some of the GDPR offences committed and ICO penalties levied over the past few years? How can we avoid becoming the next casualty? Let’s look at a few examples and break them down.
Ticketmaster
What happened?
Ticketmaster, the popular online ticket purchasing platform, was fined £1.25 million in November 2020 for failing to keep its customers’ personal data secure. The data breach was caused by a cyber-attack on a chat-bot installed on its online payment page. The attack exposed names, payment card numbers, expiry dates and CVV numbers of up to 9.4 million of Ticketmaster’s customers across Europe and the UK.
The ICO found that Ticketmaster had not adequately assessed and identified the risks of using a chat-bot on its payment page, that they had not implemented appropriate security measures to mitigate the risks, and had not identified the source of the suspected fraudulent activity in a timely manner.
Ticketmaster tried to claim that it was the third party vendor who provided the chat-bot plug-in that compromised its security measures and attempted to appeal the charge with that claim. But that vendor, Inbenta Software, said that Ticketmaster misused the code which led to exposure risk in the first place.
In any case, regulators did not accept the attempt to hang the blame on the third party and held Ticketmaster fully accountable.
What can we learn?
This case shows the critical importance of implementing appropriate security measures to avoid possible risks, and regularly monitoring all organisational activity, including any third-party applications an organisation may use, for possible issues. Had Ticketmaster had more security controls in place, which would have helped them identify the problem in a timely manner, the attack would likely have caused much less damage both to customers and to Ticketmaster.
Specifically, this case highlights the need for companies to take full responsibility for all applications they use.
Any online business in any sector, including eCommerce websites, online retailers, and online service providers such as Ticketmaster, must do everything in its power to assess all risks relating to any third-party apps it uses and thoroughly monitor them consistently for any possible security risks. If any are suspected, they must fully investigate them immediately and take any necessary action.
Failure to do so is likely to result in large fines and serious reputational damage.
Kim Doyle and William Shaw
What happened?
Kim Doyle, an employee of RAC, a motor service company, pleaded guilty and was subsequently prosecuted on charges of conspiracy to obtain unauthorised access to computer data and selling unlawfully obtained personal data.
She was sentenced to eight month’s imprisonment, suspended for two years. The data she stole included lists that she had compiled, without the permission of her employers, of road traffic accident data including partial names, phone numbers and registration numbers.
She then unlawfully transferred the data to William Shaw, the director of an accident claims management firm. Shaw was also charged in the incident and sentenced to eight months’ imprisonment, suspended for two years after he pleaded guilty to conspiracy to secure unauthorised access to computer data.
Investigators believe that Doyle made £25,000 in ‘easy money’ for transferring the information.
The details were used to make nuisance calls to RAC customers, telling them that they could be owed compensation. When investigators confiscated Doyle’s mobile, which allowed access to her work emails from home, they discovered numerous deleted WhatsApp messages between Doyle and Shaw.
Doyle and Shaw were each ordered to carry out 100 hours of unpaid work and pay £1,000 in costs. In addition, a Confiscation Order was given to the court which required Doyle to pay a benefit figure of £25,000 and Shaw a figure of £15,000, which they had to either pay within three months, or face three months imprisonment.
What can we learn?
Criminal acts that involve theft and misuse of individuals’ personal details can have serious consequences, including hefty fines, being struck off, and irreparable reputation damage. This example shows that some cases could even end in prosecution and possible imprisonment.
Mike Shaw, who heads up the Criminal Investigations Team at the ICO said: “Offenders must know that we will use all the tools at our disposal to protect people’s information and prevent it from being used to make nuisance calls.
HMRC
What happened?
Her Majesty’s Revenue and Customs (HMRC) was handed an enforcement notice for failing to get adequate consent to collect callers’ personal data.
The notice charged that HMRC collected, retained and used biometric data through its Voice ID service without having a lawful basis for doing so, without customer consent, and with little or no consideration for the data protection principles. The notice noted that an extremely large number of data subjects were affected and that these were circumstances in which there was a significant imbalance of power between it and its customers.
The commissioner’s notice required HMRC to (a) delete all biometric data held without explicit consent and (b) require all its suppliers who operate, manage, or are involved in the Voice ID system to delete all data they process for which it does not have explicit consent within 28 days of the notice, or else become subject to a fine of up to 20 million euros, or 4% of an undertaking’s total annual worldwide turnover, whichever is higher.
What can we learn?
Under GDPR, biometric data is considered special category information and is subject to stricter conditions. No one is immune from having action taken against them for failing to uphold GDPR standards, not even the UK’s official tax collection agency. On the contrary, government agencies that are entrusted with copious amounts of people’s personal information should hold themselves to the highest standards in protecting people’s data.
Steve Wood, Deputy Commissioner at the ICO, said: “Innovative digital services help make our lives easier but it must not be at the expense of people’s fundamental right to privacy. Organisations must be transparent and fair and, when necessary, obtain consent from people about how their information will be used. When that doesn’t happen, the ICO will take action to protect the public.”
What is special category data?
Under GDPR, special category data is the personal information of data subjects that is especially sensitive. Exposing such data could significantly impact the rights and freedoms of data subjects and potentially be used against them for unlawful discrimination. In this case, the special category data that may have been exposed or destroyed unlawfully could include:
- Race and ethnic origin
- Biometric data used to identify an individual
- Genetic data
- Health data
- Data related to sexual preferences, sex life, and/or sexual orientation
Seafish imports
What happened?
Seafish Imports Ltd. was issued a fine of £10,000 for sending 491,995 direct marketing messages for face masks between 23 August 2019 and 7 April 2020 to subscribers without valid consent. The notice specifically pointed out that more than half of the unsolicited marketing messages were sent during the height of the COVID-19 pandemic relating to the sale of personal protective equipment, indicating an attempt to capitalise on the pandemic.
The notice held the company responsible under section 55A of the Data Protection Act 1998 (“DPA”), and said that the penalty is in relations to a serious contravention of regulation 22 of the Privacy and Electronic Communications (EC Directive) Regulations 2003 (“PECR”), noting that the provisions of the DPA remain in force for the purposes of PECR notwithstanding the introduction of the Data Protection Act 2018.
The company was issued a monetary penalty of £10,000.
What can we learn?
This case underlines the need to keep PECR compliance in mind in addition to the GDPR.
Learn more about our PECR training
Marriott Hotel Group and British Airways
What happened?
These penalties are the largest fines to date issued under GDPR. In early July 2019, the ICO issued British Airways a £183.4 million (U.S. $230 million) fine and Marriott a £99.2 million (U.S. $124 million) fine for data breach-related violations.
In the British Airways case, the personal data of some 500,000 customers was stolen in a cyber attack on the airline by hackers diverting users to a fake website. In the case of the Marriott Hotel Group, the hotel chain suffered a data breach exposing the personal details of 339 million guests including 30 million EU citizens and 7 million UK citizens. Personal data including credit card details, passport numbers and dates of birth had been stolen in a colossal global hack of guest records.
What can we learn?
This case shows the importance of having the right procedures and systems in place to mitigate the damage of a breach. In the British Airways case, the cyber security procedures they had in place and the fact that the breach was noticed quickly helped them limit the scope of the breach. Additionally, this case shows that the bigger the company that suffers a breach, the bigger the story, which means the bigger the resulting reputational damage.
In the Marriot case, the main lesson to learn is the importance of conducting the appropriate due diligence during mergers and acquisitions.
Learn more: What should be in a data protection policy?
VinciWorks’ GDPR compliance solution: a one-stop-shop
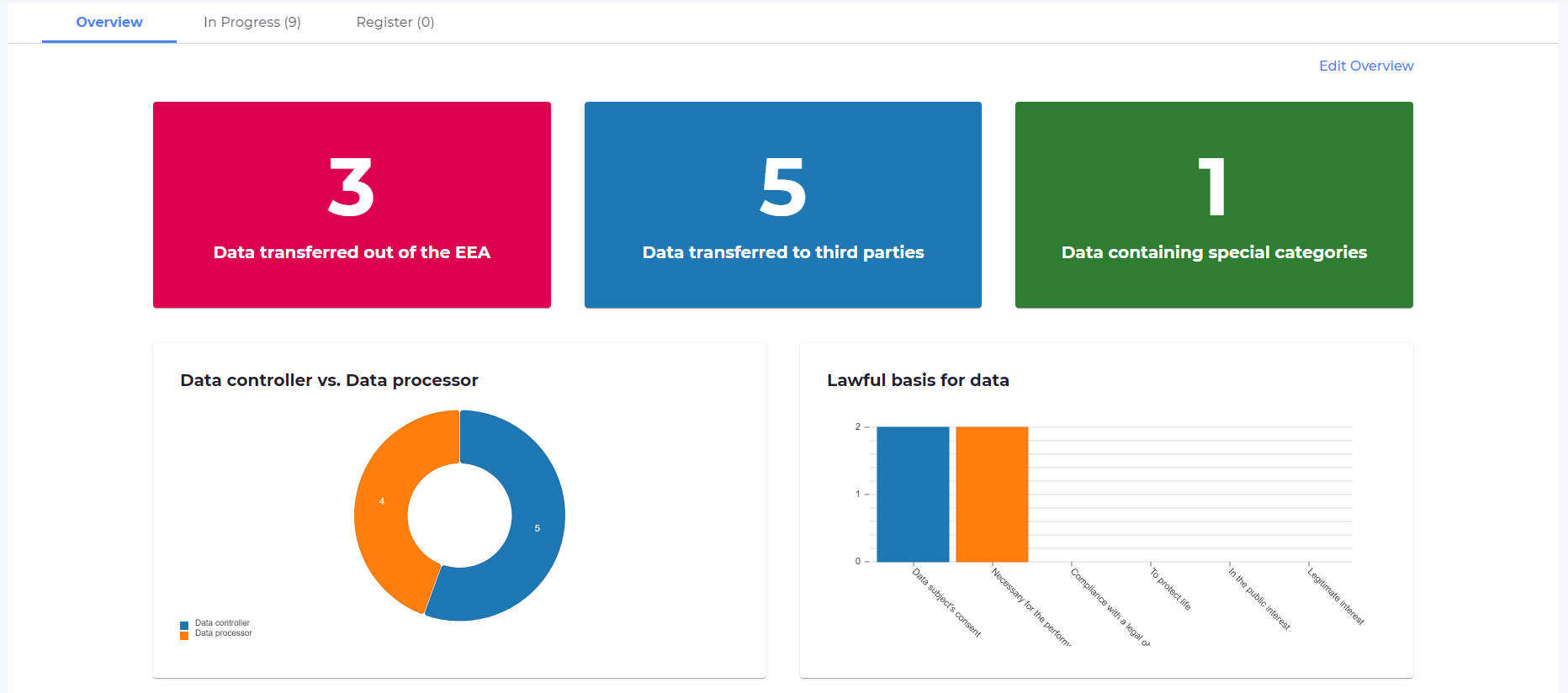
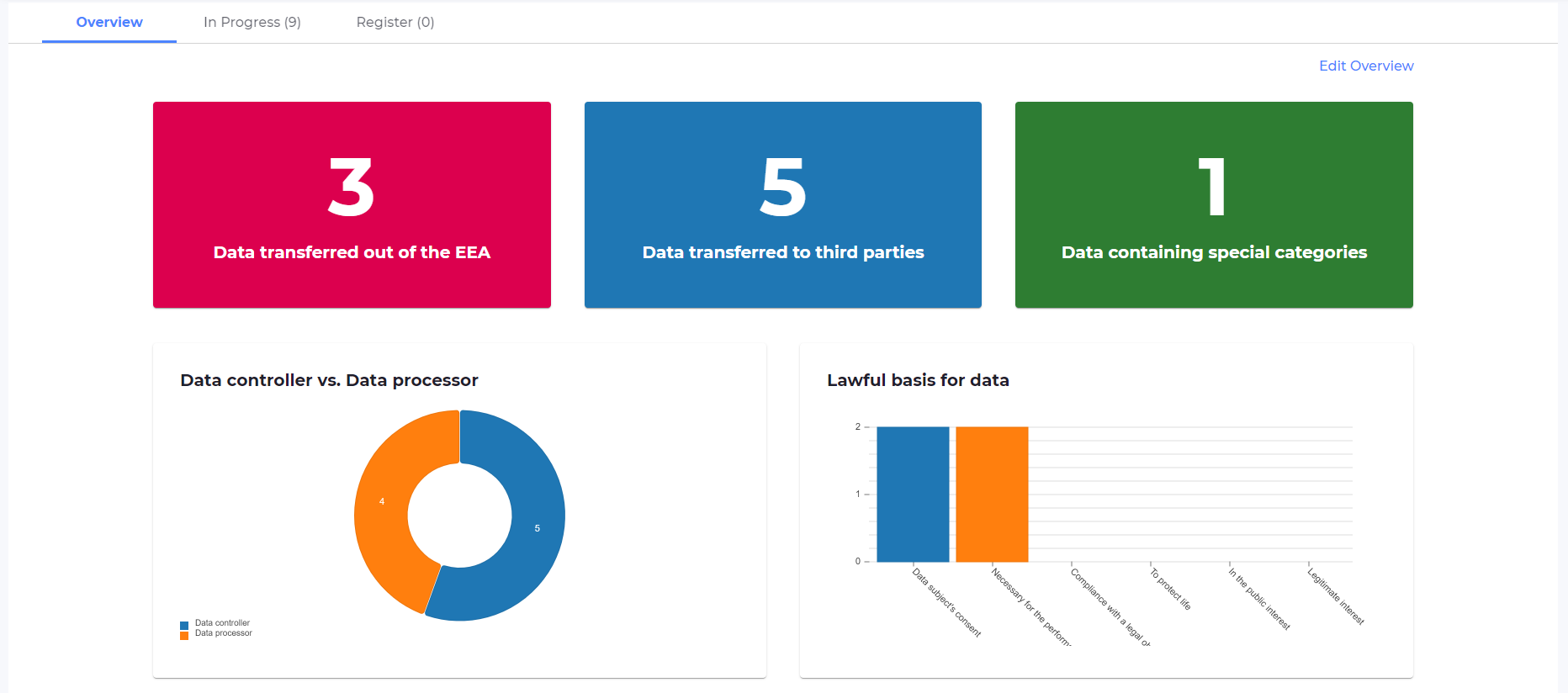
GDPR compliance should involve the entire organisation, rather than only specific departments that are deemed high risk. VinciWorks’ GDPR training solution is a one-stop-shop for complete company-wide compliance. Our suite of GDPR courses ensures that all staff are trained appropriately via interactive, customisable courses. Whether staff are well versed in GDPR or require in-depth onboarding training, we’ve got you covered.
We also offer a centralised GDPR reporting solution that allows organisations to create, track and automate all data protection registers, such as processing activities, data protection impact assessments and subject access requests.