What is social engineering?
We’ve all heard of headline-making cyber attacks and the havoc they have all too often managed to wreak. This includes the 2019 ransomware attack in Texas that held 22 cities hostage for millions of dollars and lasted for several days before being resolved. These news-worthy attacks, which are usually technical in nature and often do not require any user interaction to do their dirty work, prompt organisations large and small to invest in new technologies to strengthen their defences against these malicious and damaging infiltrations.
But there’s another type of cyber attack that, while perhaps less likely to make headlines, is equally dangerous and potentially damaging to both private individuals and organisations. Social engineering is a cyber crime tactic in which hackers use psychological manipulation to trick victims into breaching security protocols or revealing private information, thereby circumventing the usual protections that cyber security tools are supposed to provide.
Therefore, you are the first line of defence in cyber security, both in terms of protecting your own information and your company’s data. Being aware of the dangers and taking sensible cyber security measures in your personal and work life will help thwart cyber crime.
Six social engineering methods
Phishing
This all-too-common tactic involves criminals tricking people into clicking suspicious links or sharing personal information.
There are several types of phishing:
- Phishing emails: Emails that might appear to contain job offers, security warnings or invoices that, once downloaded, spread ransomware through the downloaders’ systems.
- Pharming: Cyber criminals create fake web pages that look identical to their real counterparts. They attack the domain name host and direct unsuspecting users to a scam web page where they are prompted to input sensitive details. The popular online storage site Dropbox recently suffered such an attack.
- Malvertising: Cyber attackers buy ads on trusted websites and put malware inside those ads. Unsuspecting users click the ad, thinking it will be safe since it is a reputable website, and malware is then installed on their device. Some of the most popular sites in the world, including The New York Times, Spotify, WordPress, The Atlantic and Adobe have all fallen victim to malvertising.
- Spear phishing: Hackers trawl a victim’s social media account to glean personal information in order to create a targeted attack that is more likely to trick their victim. The personal nature of the attack makes it seem more authentic and harder to detect as fraudulent.
- Whaling: A variation of phishing that targets CEOs and other executives. For example, a whaling email may appear to be from a senior executive and sent to a firm’s accounting professional with instructions to transfer funds to an outside account.
Pretexting
Pretexting is a method in which the scam artist uses some sort of story, i.e. pretext, to trick the victim into giving up personal or valuable information, or access to an account, system or service. Pretexters use a variety of forms of communication, including email, text messages, and phone calls.
Baiting
Cyber criminals dangle bait, such as a great deal or download, hoping the user will be tempted enough to “take the bait” and click on or download it. Such schemes are often found on Peer-to-Peer sites offering downloads of tempting content such as a new movie or music, or on classified or auction sites offering a supposedly amazing deal. The schemes can also be found on social networking sites or sites reached through internet searches.
Quid pro quo
A quid pro quo attack is a variation of baiting. These attacks are carried out by hackers who do not have any advanced tools at their disposal and do not carry out research as do baiting attackers. They just keep trying until they find a target. For example, they might keep trying to call random numbers and offering a service, such as technical support, until they find someone who happens to have some sort of relevant problem and falls for their bait.
Scareware
This is a form of social engineering in which hackers shock or scare their victims, for example, with the threat of a computer virus, in order to manipulate them into buying unwanted software. Usually, the threat is fictional, and the software is non-functional or is itself a virus.
Tailgating
In this tactic, a stranger tries to follow someone into a building. With so much information available about individuals and organisations online, this could be a criminal who carried out research in advance and is trying to gain access for malicious purposes.
Examples of damaging social engineering
- Employees being tricked into giving up passwords to access systems, allowing malware to be installed. Sometimes, whole systems can be at risk of being wiped out, and attackers might demand a ransom.
- Employees being tricked into giving up bank or other sensitive financial information
- Employees being tricked into giving hackers access to their computers
- Employees being tricked into downloading malicious software
Best practice: how to protect your employees from social engineering
Being aware of the dangers is the first step, as well as training your staff to recognize the signs and avoid falling prey to these often sophisticated, tricky attacks. The more trained staff are on the potential methods social engineering attackers use, the more likely that it’ll become second nature to respond appropriately and thus avoid becoming the next victim.
VinciWorks’ social engineering training
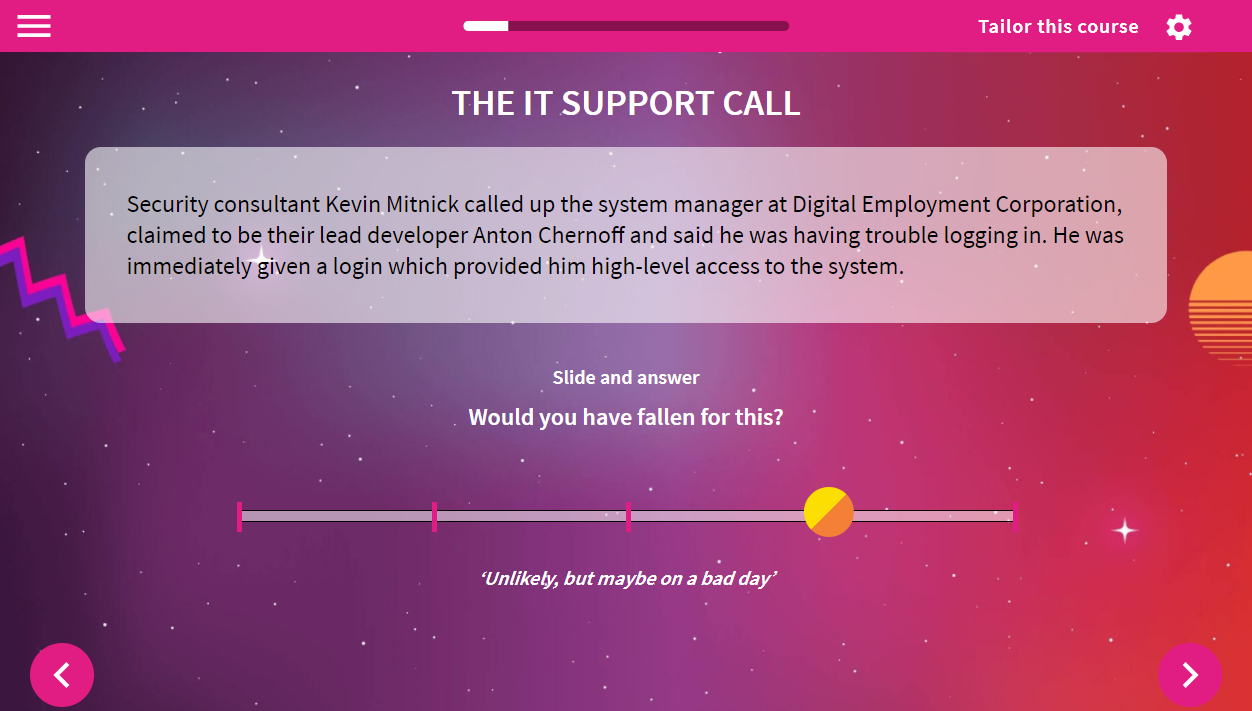
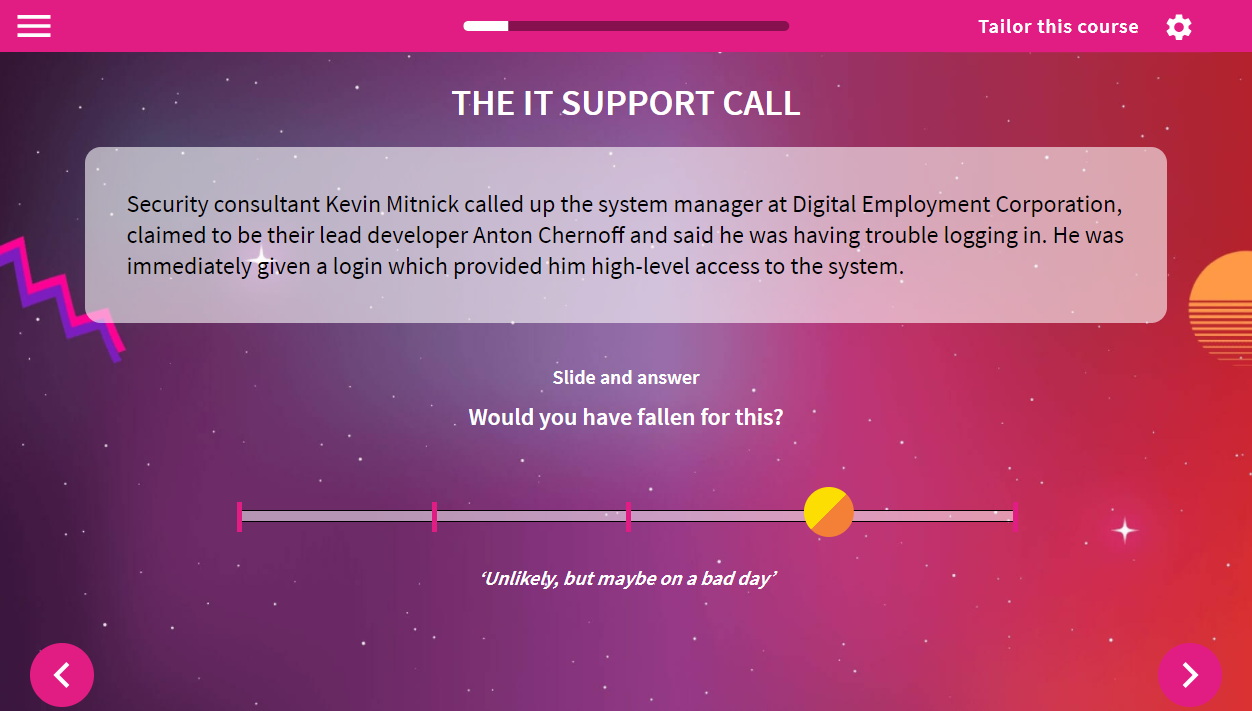
VinciWorks’ social engineering training is part of our course, Cyber Security: Journey to Safety, which features a brand new style of training that provides the ultimate in relevant learning for users. The module can be completed either as a standalone course or as part of an in-depth cyber security course. It trains users to recognise a wide range of social engineering threats and teaches them how to respond to them through exposing them to immersive scenarios, real-life case studies and interactive exercises and feedback that sets out best practice responses in a wide variety of situations.
The new cyber security course is part of our full and ever-expanding cyber security training suite that prepares users to face all cyber risks and can be configured into a multi-year training plan.