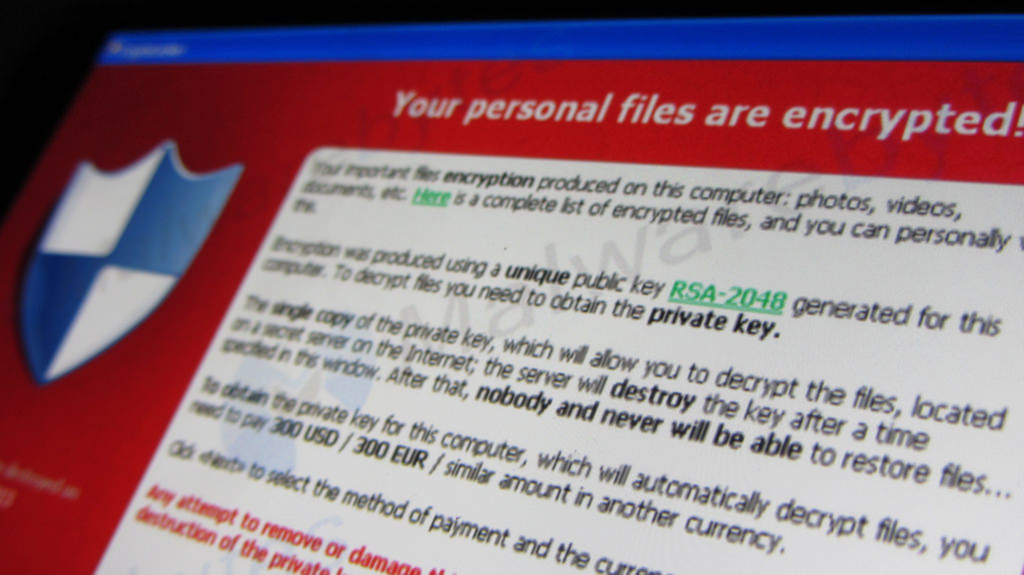
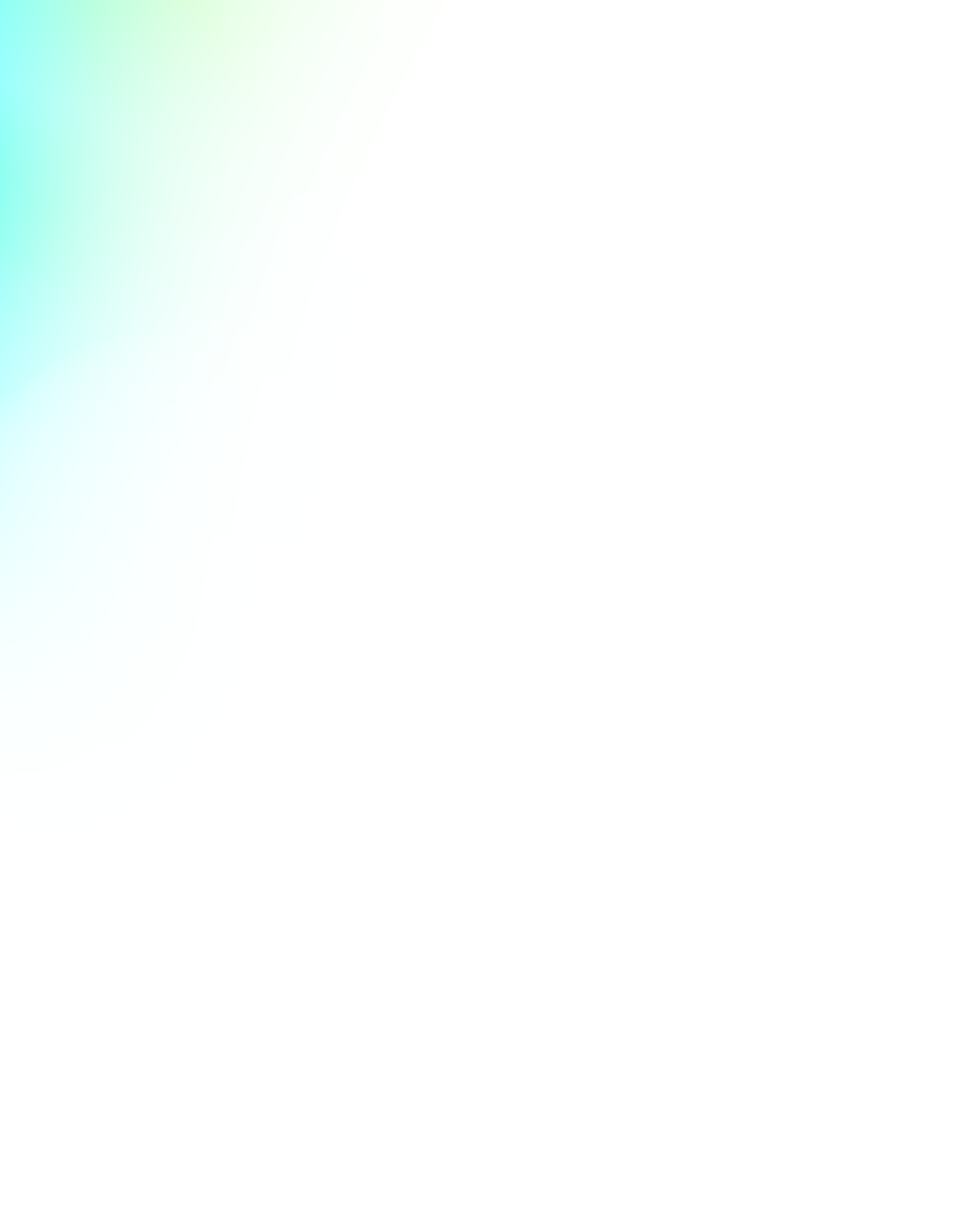Ransomware attacks computers in 150 countries
On Friday hundreds of thousands of computers were held to digital ransom as a cyber security attack spread around the world. The cyber weapon, allegedly stolen from the US National Security Agency (NSA), even locked NHS staff out of their systems, forcing hundreds of critical operations to be cancelled and staff having to turn away sick patients at the door. The attack spread quickly and installed malware onto over 200,000 computers, demanding payments of up to $600 in return for the data. With cyber security experts expecting more attacks imminently, this latest attack shows everyone needs to understand cyber security and make it a top priority.
The cyber attack that began with spam emails
The attack began with targeted phishing emails appearing to contain job offers, security warnings and invoices, as well as people’s own personal files. Once the files were unassumingly downloaded, the ransomware was able to spread across large networks. This makes understanding how to protect against cyber attacks more important than ever, with the opening of phishing emails often having the ability to affect computers across a whole network.
The importance of preventing phishing attacks
Cyber security attacks are often a result of employee error. They are fraudulent emails disguised as trustworthy emails from a reliable source such as a bank, designed to gain private information from individuals. Attacks are becoming far more targeted and sophisticated, meaning that individuals must learn to differentiate between reliable and suspect emails. With the implementation of the General Data Protection Regulation just one year away, spotting a phishing email and having processes in place to respond to a breach is incredibly vital; breaches in data protection can result in huge fines.
How to protect yourself from cyber attacks
- Keep your software up to date: Cyber criminals often exploit vulnerabilities in outdated software to gain access to your device. To reduce the risk of an attack, make sure that you keep your operating system, apps, and antivirus software up to date with the latest security patches.
- Use strong and unique passwords: Make sure that you use strong and unique passwords for all your accounts and devices. Avoid using common passwords such as “password123” or “qwerty”. Instead, use a combination of upper and lowercase letters, numbers, and special characters.
- Be cautious of phishing emails: Cyber criminals often use phishing emails to trick you into giving away your personal information. Be wary of unsolicited emails, especially those that ask you to click on a link or download an attachment. If in doubt, don’t click and delete the email.
- Use two-factor authentication: Two-factor authentication (2FA) adds an extra layer of security to your accounts. It requires you to provide a second form of identification, such as a code sent to your phone, in addition to your password. Enabling 2FA can help prevent unauthorised access to your accounts.
- Back up your data regularly: Cyber attacks such as ransomware can lock you out of your device or encrypt your files, making them inaccessible. To avoid losing important data, make sure that you regularly back up your files to an external hard drive or a cloud-based storage service.
9 Tips on How to Prevent Phishing Attacks from Affecting Your Organisation
Here is some guidance on preventing phishing attacks from affecting your organisation:
Identify phishing emails
Before we look at how to avoid being targeted by a phishing email, it’s important to understand what scammers are trying to do and how they do it. In order to gain your personal information, a typical phishing email will:
- Copy the image of a real company or person
- Take the name of a real company of person
- Include links to sites that look like real businesses
- Promote gifts, prizes and promotions
Update your Windows computer
Following the attack on Friday, Windows was able to automatically protect computers that had Windows Update enabled. While Windows has said they will provide updates for computers that run on older systems such as Windows XP (many affected computers in the NHS run on the out-of-date Windows XP, bringing to light a breach of the seventh principle of the Data Protection Act, the need to take “appropriate” technical measures against cyber attacks). However, depending on the system your computer is currently running on and the settings, these updates will not always be automatic. That being the case, you should manually download the latest version of Windows and its updates.
Don’t trust the display name
One of the methods scammers use is to copy the name of the person whose account they have hacked. They know people tend to only look at the display name, rather than the email address, to identify the sender. This method is used a lot to gain personal banking information from individuals, with the scammer posing as a banker.
Never give personal information by email
A bank, clothes retailer or in most cases a friend would never ask for personal information via email. If you receive such a request, contact the bank or friend to clarify whether they actually sent you the email. Never give out your personal information via email. It is also important to do this so the person will know their account may have been hacked.
Use reputable anti-virus software
A strong anti-virus programme will be able to scan downloaded files to see whether they contain suspicious files and can stop secret installations from malicious adverts. Make sure you use a trusted anti-virus programme to help you stop cyber attacks before they happen.
Make sure the email makes sense
Emails often look extremely trustworthy at first glance. For example, it may be easy to read an email from a colleague or client without thinking twice. However, even internal emails can be suspicious. For example, an email from the marketing department may seem plausible at first glance, but it is always worth checking. Some of these emails even contain a signature with an email address and contact number; checking that the number is correct, or quickly checking with the person whose name appears at the top of the email will authenticate the email. This could save your company a lot of money in data protection fines.
Check that the url links look authentic
Phishing emails often contain links in the body of the email and clicking on those links may send you to a web page that requests personal information, or could install malware on your computer. The best way to check the links are genuine is to hover over the links and type in the website address in a new window. You should never enter a bank’s website via a link in an email. Rather, put in the bank’s web address in a new window in your browser.
Use secure and unique passwords
Many people believe that the trick to having a good password is to have one that cannot be guessed easily and contains at least one number. However, having just one or two unique passwords for all your accounts means once one account is hacked, all your accounts become vulnerable. One of the best ways to easily create and store a unique password for each account is to use a password manager.
Never pay ransoms
Victims of cyber attacks are often offered their data back in return for a ransom. In the case of Friday’s attack, the ransom price was between $300 to $600. The National Crime Agency advises us to not pay the ransom, thus making a ransomware attack a less attractive idea for the attackers in the future.
VinciWorks’ free phishing challenge
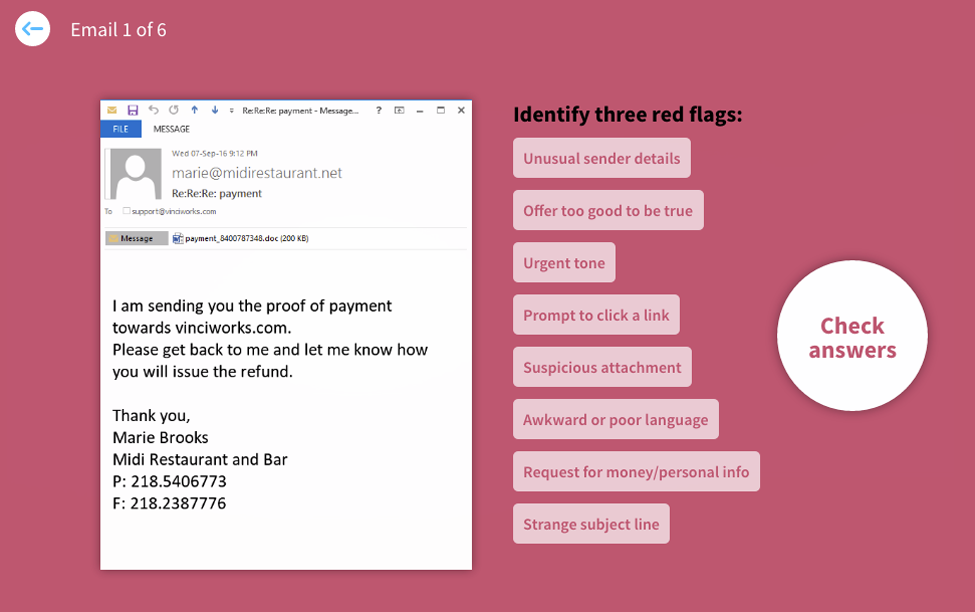
Employees are the weakest link in most cyber security attacks. The VinciWorks Phishing Challenge addresses this weakness by training employees to spot phishing emails. This five minute knowledge check can be used in any learning management system to track user completions and risk score.