The number of cyber attacks hit an all-time high last year, with the threat expected to increase in 2018. The highest profile attack, WannaCry, affected over 230,000 organisations worldwide and caused the NHS to cancel appointments and operations. Human error remains the most likely cause of cyber breaches, with phishing emails the no. 1 tactic used by attackers. In more sophisticated attacks, such as spear phishing attacks, phishing emails will target individuals or organisations, being more personalised to include the victim or company’s name. The results of such an attack can be devastating, often resulting in sensitive information being compromised and financial repercussions.
Two new courses added to cyber security suite
VinciWorks’ cyber security suite has now been updated to help protect staff from the latest threats. We have added two new short courses, allowing users to learn how to protect themselves and their organisation in just five minutes.
Ransomware micro course

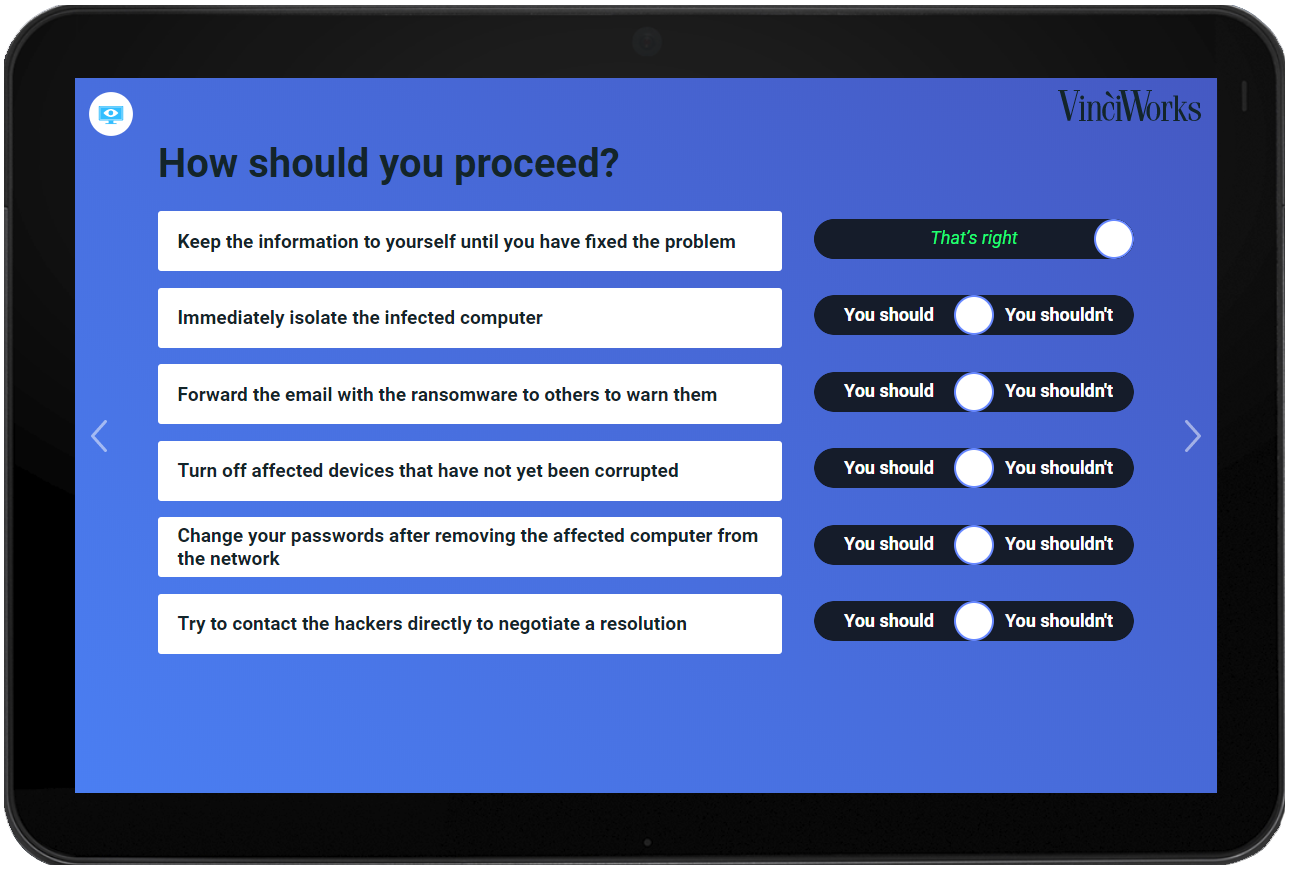
Ransomware attacks are becoming ever more sophisticated and ferocious. Clicking the wrong link can let attackers hold your entire business hostage. Learn how to protect yourself and your business from being a target in the next digital hostage crisis with this short course.
The course covers:
- Understanding what ransomware is and the dangers such attacks present
- Key definitions related to ransomware, such as “phishing”, “spear phishing”, “malware” and “Bitcoin”
- 2017 ransomware attacks and how they happened
- Visual examples of how attacks happen
- Guidance on how to avoid being the target of ransomware attacks
- What to do in case of an attack
- Assessment to review what has been learnt
Phishing Challenge 2.0
We’ve all seen emails purporting to be from a bank or credit card company, but some phishing emails are targeted and very well disguised. Following the release of Phishing Challenge last year, Phishing Challenge 2.0 presents a new catalogue of emails, with users having to identify the red flags in each email.
The course:
- Enables you to identify high-risk employees
- Produces a report with each employee’s phishing risk score
- Educates users on how to spot suspicious emails
- Challenges users to spot red-flags in real phishing emails
Engaging modular cyber security course
Our mobile friendly cyber security course is appropriate for all staff and is also part of our cyber security training suite. It challenges learners to reassess their attitudes towards cyber security. It educates users on the sophistication of modern hackers and drives users to adopt safer cyber behaviours. Since its original release, six new apps have been added to the course.
The course is designed as a 20 minute journey through a series of interactive apps. Each app tackles a different topic and provides actionable advice for improving cyber security.
After completing the course users will understand:
- How easy it is for any employee to cause irreparable damage to their company
- How to identify phishing emails and unsafe websites or links
- The personal cyber security weak points qand how to improve them
- how to identify and avoid social engineering
- The dangers of using the same password on multiple sites and using insecure passwords
Cyber security learning plan calendar
VinciWorks’ suite of cyber security micro courses enables you to deliver short regular training throughout the year to ensure that staff remain vigilant. In a review of cyber security training at multiple organisations, we found that regular intervals of short training, in coordinated company-wide campaigns, is the most effective way to keep the cyber conversation top-of-mind.
To help you plan your cyber awareness campaign, we have prepared a customisable annual calendar with suggested dates for rolling out online cyber security training. You can download the cyber security learning planner here.
Advanced analytics and text customisation
All the courses in the suite can be customised (at a cost) to include internal information about cyber security policies. Further, we can customise Phishing Challenge 2.0 to collect advanced analytics, allowing your organisation to identify cyber weaknesses. These analytics include:
- Highest risk employees
- Highest risk departments
- Which emails caught out your staff
- Your organisation compared to others
- Detailed results for every user
If you have any questions regarding customisations or any of our cyber security training, feel free to contact us using the form below.