Cyber training is most effective when delivered in short, micro-learning modules and users retain the information best when it is relevant to their individual circumstances and level of expertise. We may not need to teach IT professionals about password protection, just as the average staff member doesn’t need to know the technical specifications of the business’ firewall.
Cyber Security: Journey to Safety is the latest addition to our comprehensive cyber awareness training suite. The training takes course building and personalisation to the next level. Using our new builder, you can dynamically configure the training to cover topics relevant to your organisation. The builder can be used multiple times to create different courses for different job roles, or micro-courses for a cyber awareness drip campaign. All of this configuration happens instantaneously, with live previews of the results.
Build your custom training now
The course focuses on the areas of cyber security that place businesses most at risk and takes an innovative, interactive approach to training.
Included module packs
Each module pack contains a number of short, direct lessons that can be mixed and matched depending on the individual circumstances of each user.
- The basics of cyber security
- Password management
- Ransomware
- Phishing
- Social Engineering
- Social media
- Cyberbullying
- Email@risk
- Info classification
With over 90 minutes of content to choose from, users can spend time thinking through how scammers exploit oversharing on LinkedIn to setting up a LastPass account. Power users can also breeze through the basics and key lessons the business needs them to know in as little as fifteen minutes, focusing on things like creating a strong password, knowing how to spot ransomware and avoiding the pitfalls of sending the wrong email.
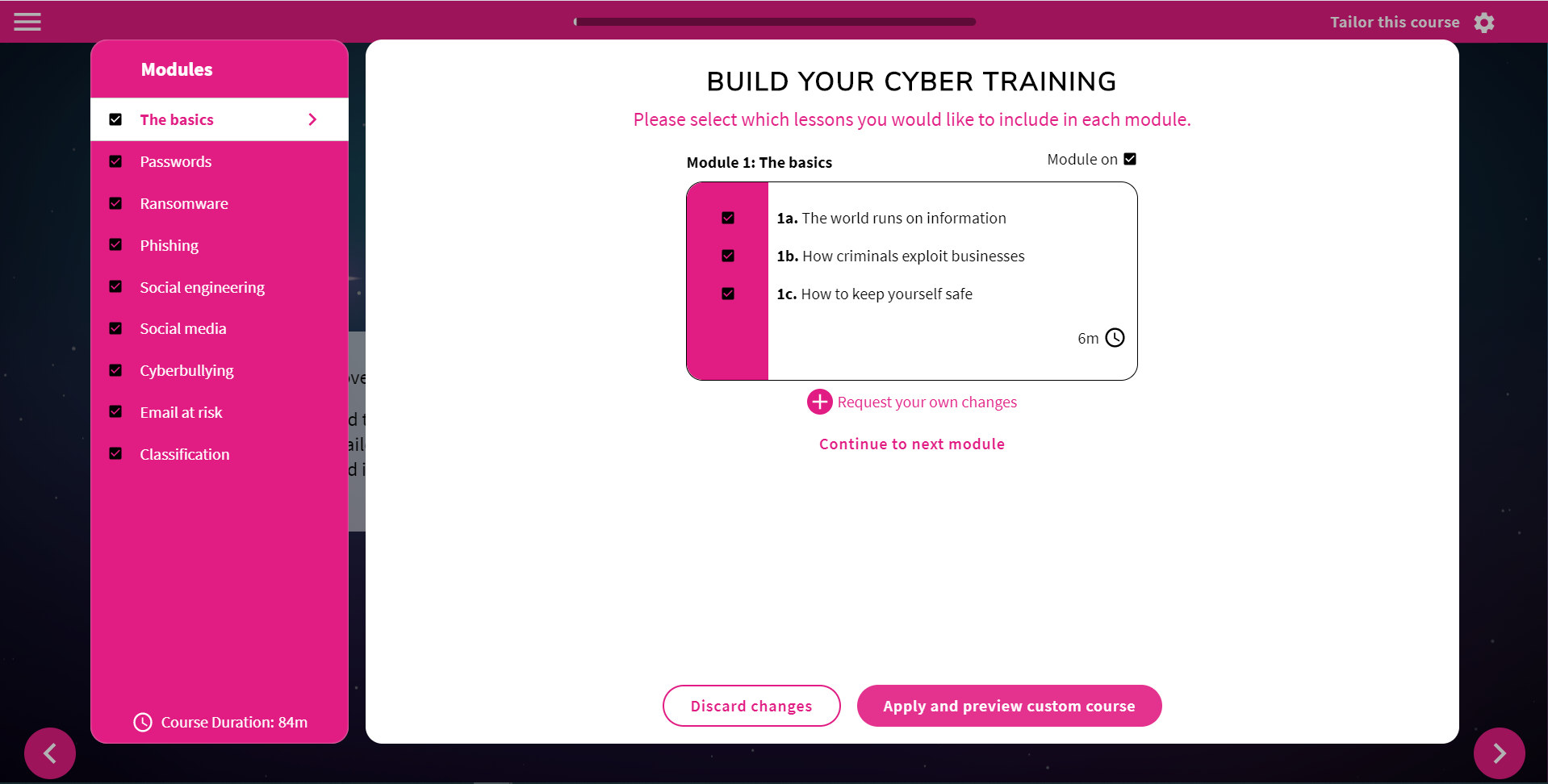
How does the course builder work?
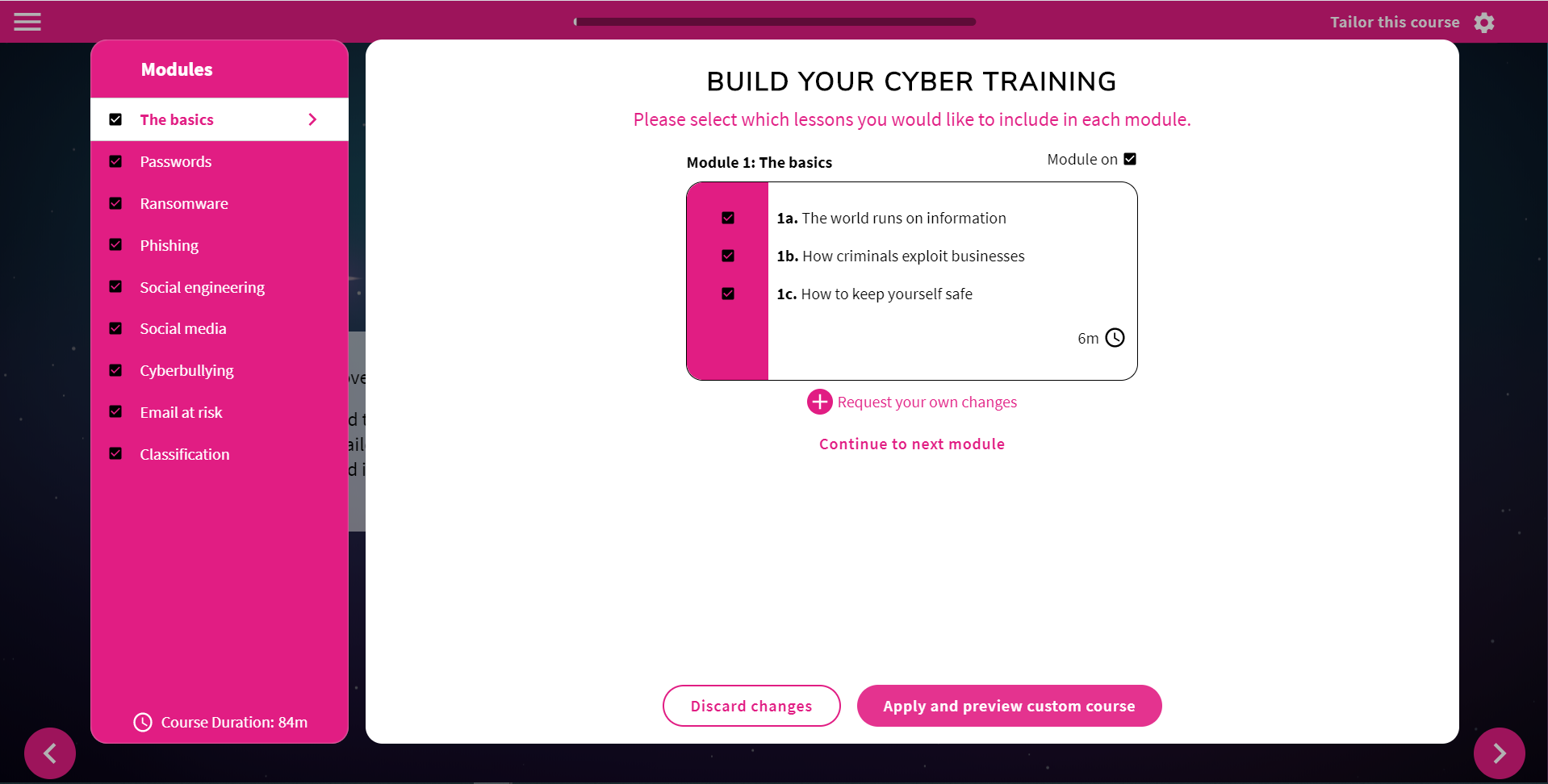
Ensuring each staff member takes the cyber security course that is 100% relevant to each user is a challenge for compliance managers. Some employees, such as IT staff, may well have a better understanding of the topic while also requiring more in-depth training around other areas. Marketing staff, on the other hand, will need to become familiar with the cyber security risks surrounding online reputation and social media.
Our course builder allows administrators to choose exactly which aspects of cyber security compliance are covered in the course without having to review the entire text of the course and manually edit each word that isn’t appropriate for a particular user or group of users. Admins are presented with the full outline of the course and can choose which modules should be included, as well as which units within each module should be excluded from the course. They can request specific changes at any point in the course and can see exactly how the length of the course is affected by every change they implement.
Course features

- A dynamic builder to create the right course for the right user
- Interactivity built into every page
- A fresh and bold retro-futuristic design
- Personal risk assessments and individualised activities
- Real-life examples of cyber attacks and compliance failures
Course outcomes
- Understand the real-world impacts of cyber security breaches
- Know how to keep yourself and your business safe online
- Be aware of data scammers can use to create targeted phishing attacks
- Assess the risks of using different websites and online tools
- Learn to create a strong password and use password managers
- Protect personal and business data from cyber attackers
If you like to be updated when the course is available, please complete the short form below.