PHISHING ASSESSMENT
The following risk assessment is designed to evaluate your risk of phishing attack.
It is a short snippet from the new VinciWorks course Cyber Security: Practical Applications.
PHORMS of PHISHING
Our IT department does a good job of protecting us from external attacks. But since we hold valuable client and other business data, we are a target for potential attackers. Instead of targeting us with a technical attack, hackers are increasingly targeting employees instead.
Phishing
"Phishing" is when attackers fraudulently pose as a known or trustworthy person to trick you into revealing information. This is usually done via email, but phishing also take place by phone, text message or other means. We’ve all seen emails purporting to be from a bank or credit card company, but some phishing emails are targeted and very well disguised.
Let’s see if you can pick out the warning signs!
Email 1 of 6
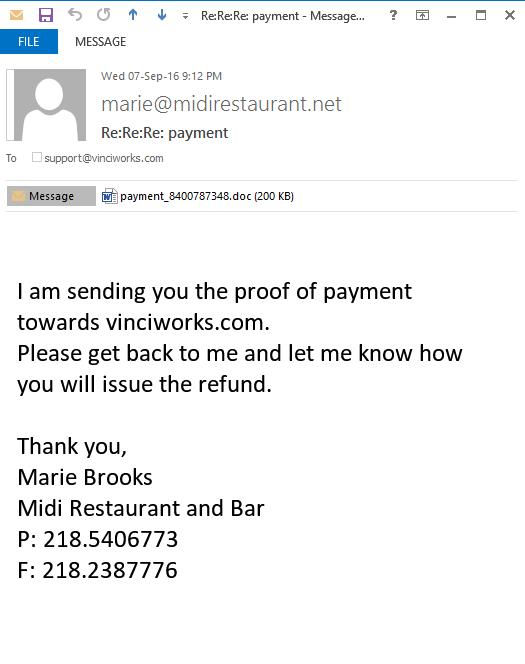
Identify three red flags:
- Unusual sender details
- Offer too good to be true
- Urgent tone
- Prompt to click a link
- Suspicious attachment
- Awkward or poor language
- Request for money/personal info
- Strange subject line
Email 2 of 6
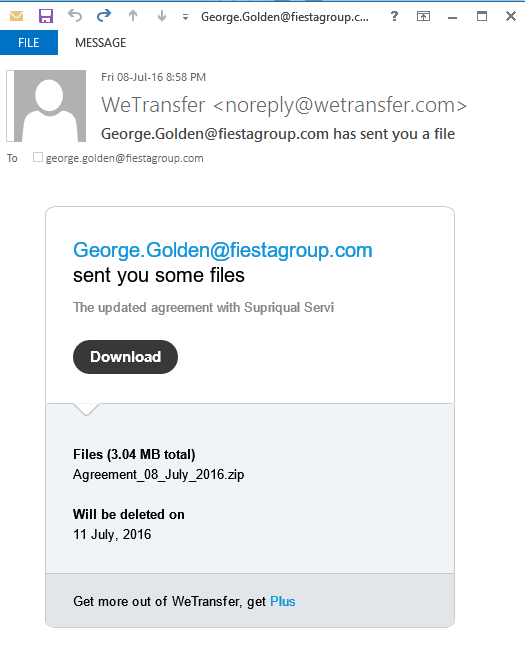
Identify three red flags:
- Unusual sender details
- Urgent tone
- Prompt to click a link
- Suspicious zip file
- Awkward or poor language
- Request for money/personal info
- Identical "to" and "from" fields
- Offer too good to be true
Email 3 of 6
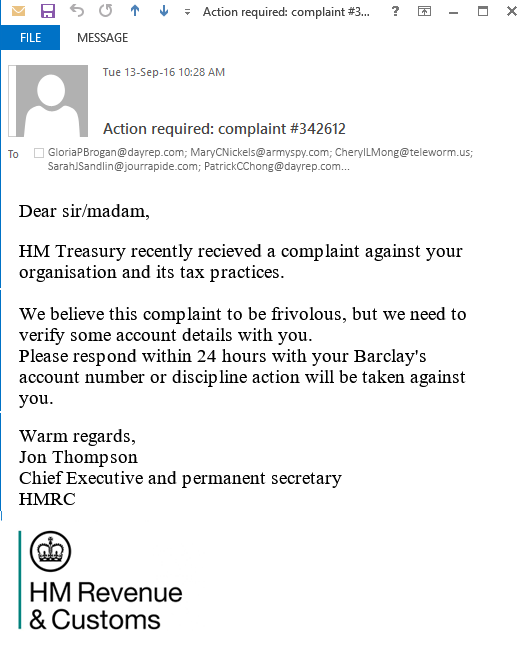
Identify six red flags:
- Unusual sender details
- Many random recipients
- Urgent tone
- Prompt to click a link
- Suspicious attachment
- Awkward or poor language
- Request for money/personal info
- Generic content
Email 4 of 6
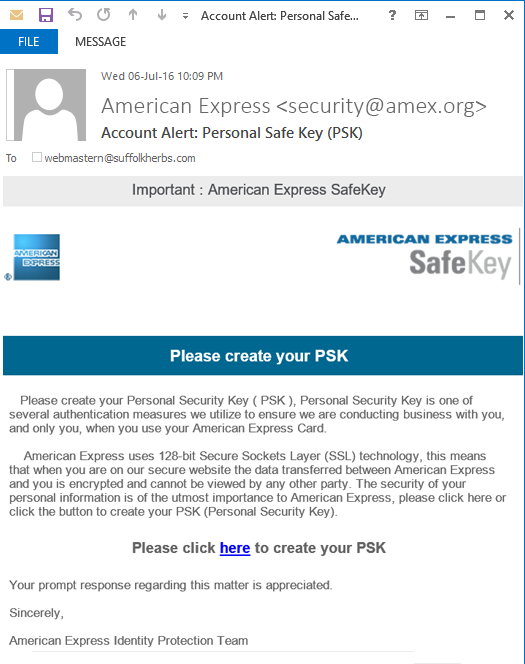
Identify seven red flags:
- Unusual sender details
- Unusual recipient address
- Generic subject line
- Urgent tone
- Prompt to click a link
- Suspicious attachment
- Awkward or poor language
- Request for money/personal info
Email 5 of 6
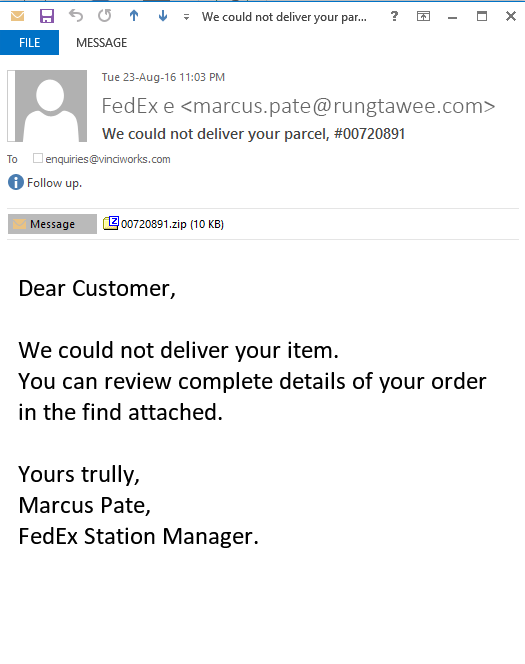
Identify three red flags:
- Unusual sender details
- Generic subject line
- Urgent tone
- Prompt to click a link
- Suspicious attachment
- Awkward or poor language
- Request for money/personal info
- Hovering over a link displays an unexpected address
Email 6 of 6
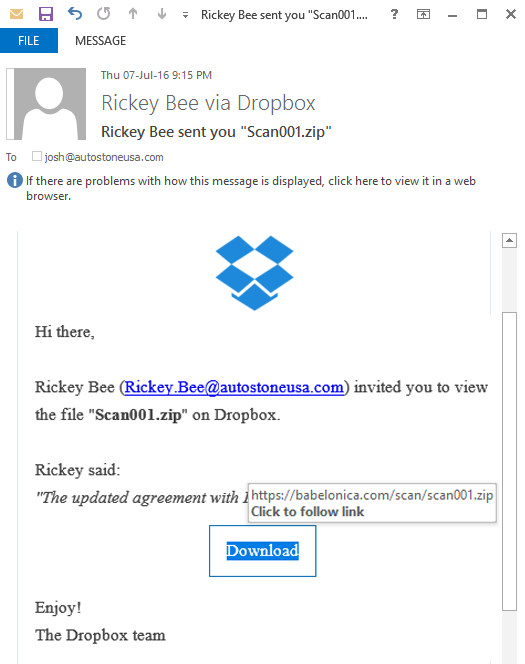
Identify five red flags:
- Unusual sender details
- Generic subject line
- Urgent tone
- Prompt to click a link
- Suspicious zip file
- Awkward or poor language
- Request for money/personal info
- Hovering over a link displays an unexpected address
Over time, hackers have continued to develop new tactics. Building on the phishing theme, other varieties include:
Spear phishing
Spear phishing is an email that appears to be from an individual or business that you know. It is not the same email sent to a large volume of recipients but is specifically written for you, based on research about you. This makes it seem that much more authentic and harder to detect as fraudulent.
Whaling
Whaling is a variation of phishing, but to larger targets, such as CEO’s and other executives. Whaling emails are carefully researched and crafted messages sent to specific individuals at a firm. For example, a whaling email may appear to be from a senior executive and sent to a firm’s accounting professional with instruction to transfer funds to an outside account.
Read more: San Jose, CA company loses over $40 million in cyber fraud whaling
Red Flags - here’s what to look out for:
- 1 Email sender’s name and address are inconsistent or unusual.
- 2 Subject line is generic, such as “your account “, “valued customer" or” invoice”.
- 3 The message does not contain your email address in the ‘To’ field.
- 4 There is an urgent tone, prompting you to take immediate action.
- 5 The email prompts you to click on links and take further action.
- 6 You do not recognise the sender’s name, or there is no sender or contact information listed in the message that you could verify elsewhere.
- 7 There is an attachment to the email with a .zip or other unrecognised file extension.
- 8 The message is written in awkward or poor language.
- 9 Hovering over a link displays an unexpected address. Look out for similar variations, e.g. www.loydsbank.com.
And the most important red flag of all:
- 10 The email makes you suspicious. If something feels wrong, play it safe.
Cyber security course by VinciWorks
This assessment is just a short snippet of the VinciWorks cyber security course.
The course, appropriate for all staff, teaches people about the dangers of using online communications to conduct business. After completing the course users will:
- Understand how easy it is for users with any technical background to cause irreparable damage to the brand
- Know how to identify and report cyber attacks including phishing attacks, fake website or suspicious file attachments
- Know how to identify and avoid social engineering
- Understand the dangers of using the same password on multiple sites and using insecure passwords





